- Home
- »
- Next Generation Technologies
- »
-
Software Defined Perimeter Market Size, SDP Industry Report, 2025GVR Report cover
![Software Defined Perimeter Market Size, Share & Trends Report]()
Software Defined Perimeter Market Size, Share & Trends Analysis Report By Enforcement Point (Gateway, Controller, End-Point), By Deployment, By Organization, By Application, And Segment Forecasts, 2019 - 2025
- Report ID: GVR-2-68038-966-1
- Number of Pages: 180
- Format: Electronic (PDF)
- Historical Range: 2015 - 2016
- Industry: Technology
Industry Insights
The global software defined perimeter market size was estimated at USD 2.12 billion in 2017 and is anticipated to expand at a CAGR of 18.4% over the forecast period. Increasing adoption of cloud technology, need for scalable and programmable security architecture, and stringent regulations and data compliance requirements on the data are anticipated to drive the growth. Software defined perimeter (SDP) is a security-based approach that diminishes network-based attacks. In this, a perimeter is created on the network dynamically to protect the data present in a cloud, in the demilitarized zone, and data centers. Emergence of Internet of Things (IoT) and changing Bring Your Own Device (BYOD) trends are expected to further fuel the growth.
Adoption of cloud based services have led to lowering the threats on network. Traditional data centers and servers cannot be protected with traditional perimeter defense techniques such as firewalls, thus increasing the threat of network attacks against application infrastructure. Thus, lack of awareness about security coupled with lack of industry standards restrain expansion of the SDP market.
SDP safeguards all the end points that are making numerous attempts to access the said infrastructure as authenticated. Hence, all the unauthorized networks are made unapproachable, and protect the defined network with the perimeter. These also provide a privilege to reduce the attacks on the network by hiding the network resources unauthorized or unauthenticated users.
SDP enables various small and large organizations to provide controllable, protected and reactive access to networked systems. Thus, it is much cheaper and easier to deploy SDP than the other firewalls, and other related technologies. SDP allows to stop the various forms of attacks such as Distributed Denial of Service (DDoS), Man-in-the-Middle (MITM), Server Query (OWASP10), and Advanced Persistent Threat (APT).
Many enterprises dependent on Multi Factor Authentication (MFA) and Virtual Point-to-Point (VPN), manage admittance to the global supply chain linkage are exposed to moving malware that extents from the devices of authorized users. There are possibilities where an enterprise is able to deploy the newest form of end point security on the devices.
Enforcement Point Insights
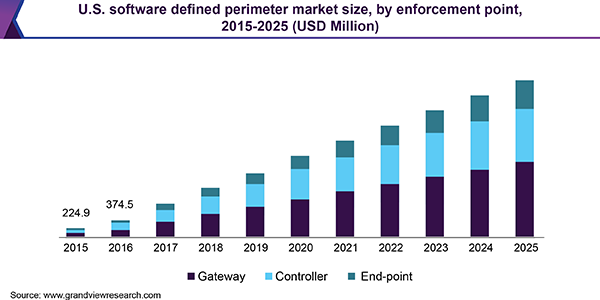
The gateway segment held the largest software defined perimeter (SDP) market share in 2017, while end-point segment is anticipated to expand at the fastest CAGR over the forecast period. The client is configured in real-time to ensure the certifications and only connects to the authorized user for authenticated services. The controller segment has various functions such as Issuing Certificate Authority and Identity Provider. Thus, the controller configures the client and gateway in real-time. As the identity of the requesting device is verified with the provision of an authorization, the Gateway is delivered with the IP address and certificates with the client.
Organization Insights
SDP requires users to provide multiple authentication to confirm whether the users are secure to enter the network or not. This multiple authentication enables large organizations to identify an illegal user although the user holds legal user credentials.
Large enterprises held the largest market share in 2017. These organizations hold huge data on the finance, accounts, company data and others. This needs to be securely stored as well as securely utilized by the authorized users. The users perform several confidential tasks, SDP continuously monitors the behavioral changes occurring in the environment.
Application Insights
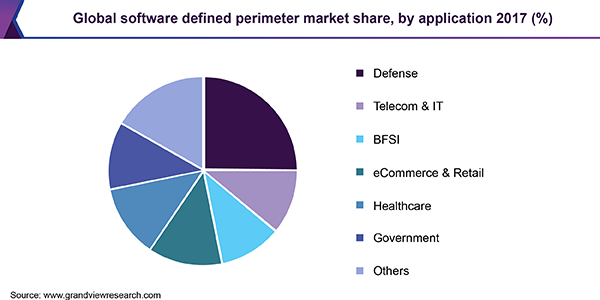
Software defined perimeter originated in the defense services and is most widely used in defense applications. The Banking, Financial and Insurance Services (BFSI) sector is also anticipated to hold the major market share. Telecom and IT segment is expected to register the fastest CAGR over the forecast period owing to the high data breaches, and accessing the restricted infrastructure. Demand for streamlined security of the structure is anticipated to further fuel the adoption of SDP.
In any organization, if the traditional perimeter model is breached, it gets easier to access the privileged data of an organization. Nowadays, BFSI, telecom, government, healthcare, and others are prone to increasing data traffic. This traffic drags the unauthorized user to access the perimeter. Thus, with the usage of SDP, irrespective of their network or location, users that are legitimate to access any protected resources are completely authenticated before they link.
Regional Insights
Asia Pacific is expected to expand at the fastest rate over the forecast period. The region holds the base of telecom service providers, ecommerce and retailers, and others. The region also holds the prominent number of startups. These startups are anticipated to adopt cloud based solutions in the forthcoming years. Also, the growing need to secure the data, stringent regulations, and changing BYOD trends are expected to drive the market over the forecast period.
North America held the largest market share in 2017, owing to the adoption of software defined perimeter large enterprises to offer high performance, efficiency, and to avoid data insecurity over the heavy traffic network.
Software Defined Perimeter Market Share Insights
Key players such as Intel Corporation; Cisco Systems Inc.; Juniper Networks; Fortinet Inc.; Symantec Corporation; Check Point Software Technologies Ltd.; Catbird Networks Inc.; Certes Networks; EMC RSA; and Palo Alto Networks Inc.; among others hold significant position in the SDP market.
Various strategies have been adopted by these companies to maintain the market position. The providers are aggressively investing in R&D to remain competitive. New software launches for security purposes have been an important segment in the overall market growth. For instance, in November 2017, Safe-T launched a new solution - Software Defined Access. In May 2017, Verizon has launched SDP service that enables enterprises to identify and block cyber-attacks by creating a virtual perimeter around the network.
Report Scope
Attribute
Details
Base year for estimation
2017
Actual estimates/Historical data
2015 - 2016
Forecast period
2018 - 2025
Market representation
Revenue in USD Million and CAGR from 2018 to 2025
Regional scope
North America, Europe, Asia Pacific, South America, Middle East & Africa
Country scope
U.S., Canada, Mexico, U.K., Germany, France, China, India, Japan, Brazil
Report coverage
Revenue forecast, company share, competitive landscape, growth factors and trends
15% free customization scope (equivalent to 5 analyst working days)
If you need specific information, which is not currently within the scope of the report, we will provide it to you as a part of customization
Segments Covered in the ReportThis report forecasts revenue growth at global, regional, and country levels and provides an analysis of the latest industry trends in each of the sub-segments from 2015 to 2025. For the purpose of this study, Grand View Research has segmented the global software defined perimeter market report on the basis of enforcement point, deployment, organization, application, and region:
-
Enforcement Point Outlook (Revenue, USD Million, 2015 - 2025)
-
Gateway
-
Controller
-
End-Point
-
-
Deployment Outlook (Revenue, USD Million, 2015 - 2025)
-
On-Premise
-
Cloud
-
-
Organization Outlook (Revenue, USD Million, 2015 - 2025)
-
Small and medium enterprises
-
Large enterprises
-
-
Application Outlook (Revenue, USD Million, 2015 - 2025)
-
Defense
-
Telecom & IT
-
BFSI
-
E-commerce & Retail
-
Healthcare
-
Government
-
Others
-
-
Regional Outlook (Revenue, USD Million, 2015 - 2025)
-
North America
-
The U.S.
-
Canada
-
Mexico
-
-
Europe
-
The U.K.
-
Germany
-
France
-
-
Asia Pacific
-
China
-
India
-
Japan
-
-
South America
-
Brazil
-
-
Middle East & Africa
-
Share this report with your colleague or friend.
![gvr icn]()
NEED A CUSTOM REPORT?
We can customize every report - free of charge - including purchasing stand-alone sections or country-level reports, as well as offer affordable discounts for start-ups & universities. Contact us now
![Certified Icon]()
We are GDPR and CCPA compliant! Your transaction & personal information is safe and secure. For more details, please read our privacy policy.
We are committed towards customer satisfaction, and quality service.
"The quality of research they have done for us has been excellent."