- Home
- »
- Network Security
- »
-
Security Information And Event Management Market, 2033GVR Report cover
![Security Information And Event Management Market Size, Share & Trends Report]()
Security Information And Event Management Market (2025 - 2033) Size, Share & Trends Analysis By Solution (Software, Service), Deployment (Cloud, On-premise), By Enterprise Size, By End-use (BFSI, IT & Telecom, Retail & E-commerce), By Region, And Segment Forecasts
- Report ID: GVR-4-68040-089-9
- Number of Report Pages: 120
- Format: PDF
- Historical Range: 2021 - 2024
- Forecast Period: 2025 - 2033
- Industry: Technology
- Report Summary
- Table of Contents
- Interactive Charts
- Methodology
- Download FREE Sample
-
Download Sample Report
Security Information And Event Management Market Summary
The global security information and event management market size was estimated at USD 5.12 billion in 2024 and is projected to reach USD 18.22 billion by 2033, growing at a CAGR of 15.3% from 2025 to 2033 due tothe increasing sophistication and frequency of cyberattacks across industries. As organizations face advanced threats such as ransomware, phishing, and insider attacks, the need for real-time monitoring, threat detection, and rapid incident response becomes critical.
Key Market Trends & Insights
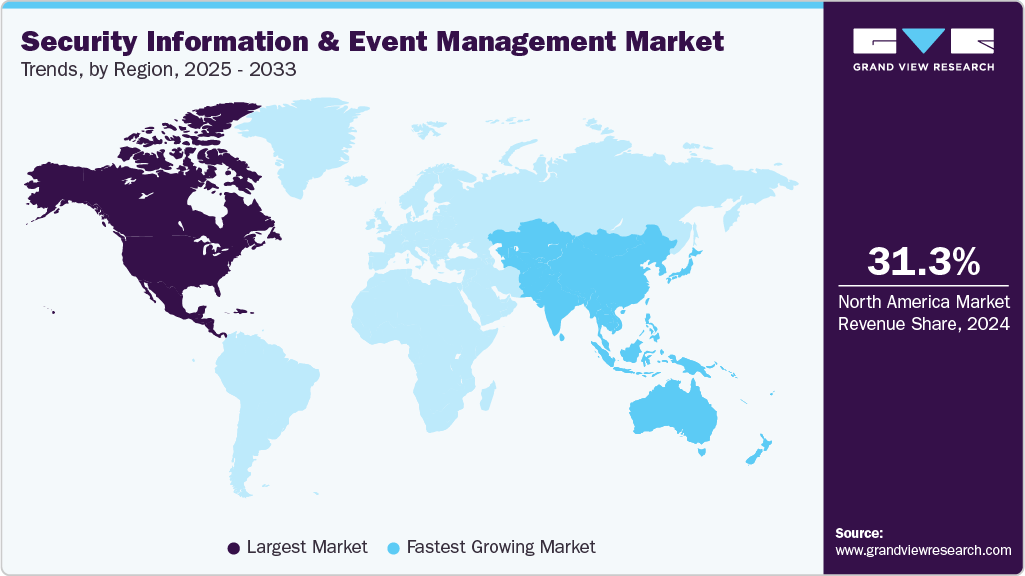
- North America security information and event management (SIEM) dominated the global market with the largest revenue share of 31.3% in 2024.
- The security information and event management (SIEM) market in the U.S. is expected to grow significantly at a CAGR of 10.3% from 2025 to 2033.
- By solution, software led the market and held the largest revenue share of 64.5% in 2024.
- By deployment, the cloud-based segment held the dominant position in the market and accounted for the largest revenue share in 2024.
- By end-use, the IT and telecom segment dominated the market and accounted for the largest revenue share in 2024.
Market Size & Forecast
- 2024 Market Size: USD 5.12 Billion
- 2033 Projected Market Size: USD 18.22 Billion
- CAGR (2025-2033): 15.3%
- North America: Largest market in 2024
- Asia Pacific: Fastest growing market
SIEM solutions consolidate and analyze vast volumes of security data from networks, endpoints, and applications, enabling enterprises to identify vulnerabilities, detect anomalies, and comply with stringent regulatory requirements. The growing emphasis on cybersecurity resilience, especially with remote work and cloud adoption, has accelerated the adoption of SIEM platforms, making them an essential tool for protecting sensitive data and maintaining operational continuity.With the rise of stringent data protection and privacy regulations such as GDPR, HIPAA, and CCPA, organizations are under increasing pressure to monitor, log, and report security events. SIEM solutions help businesses maintain compliance by providing audit trails, automated reporting, and continuous monitoring capabilities. As regulatory frameworks become more complex and enforcement stricter, organizations are increasingly investing in SIEM tools to avoid penalties and safeguard their reputation.

In addition, trends like proactive threat hunting capabilities and low-code/no-code analytics empower security teams to analyze historical data, build custom alerts and dashboards, and anticipate threats without extensive technical expertise, ensuring that SIEM platforms remain agile and adaptive in dynamic cybersecurity landscapes. For instance, in May 2025, Exabeam partnered with Vectra AI to combine their strengths in security analytics and AI-driven threat detection. This collaboration enables faster identification of potential threats across networks and cloud environments. By automating routine security operations, it reduces manual workloads for analysts and strengthens overall cloud security posture.
Solution Insights
The software segment dominated the market and accounted for the revenue share of 64.5% in 2024. Stand-alone SIEM platforms are increasingly being integrated with or replaced by solutions that offer broader capabilities, most notably Security Orchestration, Automation, and Response (SOAR). The demand for SIEM software that natively includes or seamlessly integrates with SOAR modules is growing because it directly addresses the cybersecurity skills gap.
The services segment is anticipated to grow at the highest CAGR during the forecast period. The growing volume of alerts and the critical need for 24/7 monitoring are driving the expansion of Managed Security Services (MSS) and Managed Detection and Response (MDR) offerings that are built around SIEM technology. Many organizations, particularly mid-sized businesses, find it prohibitively expensive and challenging to recruit and retain a full team of skilled security analysts to operate their SIEM around the clock.
Deployment Insights
Thecloud segment dominated the market and accounted for the largest revenue share in 2024. As enterprises accelerate digital transformation, the adoption of cloud and hybrid infrastructures has become the norm, bringing with it complex, distributed environments that generate vast amounts of telemetry. Traditional on-premises SIEM solutions often lack the flexibility and scalability to process and analyze these dynamic data flows effectively, creating visibility gaps.
The on-premise segment is expected to grow at a significant CAGR during the forecast period. Stringent data sovereignty and regulatory compliance are significant drivers for on-premise SIEM solutions. Industries such as government, defense, finance, and healthcare operate under extreme regulatory pressures, often mandating that sensitive data never leaves the organization's physical control. Regulations may explicitly prohibit storing certain types of classified, personally identifiable information (PII), or financial data on third-party servers, especially those located in different countries.
Enterprise Size Insights
Thelarge enterprise segment dominated the market and accounted for the largest revenue share in 2024. Large enterprises operate extensive IT infrastructures, spanning multiple on-premises data centers, hybrid environments, and multi-cloud deployments. The complexity of these environments generates massive volumes of security data from servers, endpoints, applications, network devices, and cloud services. SIEM platforms help centralize and correlate this data, providing real-time visibility and advanced threat detection across the enterprise. The need to manage diverse, distributed systems efficiently drives large-scale SIEM adoption
The SMEs segment is expected to grow at a significant CAGR during the forecast period. Vendors are offering cloud-based and subscription-based SIEM solutions tailored for SMEs, which are cost-effective and easy to scale according to business needs. Unlike traditional enterprise SIEM deployments, these solutions reduce upfront investment and IT complexity, making advanced security accessible to smaller organizations.
End-use Insights
The IT and telecom segment dominated the market and accounted for the largest revenue share in 2024. The IT and telecom sector operates extensive networks, data centers, cloud services, and edge computing environments that generate enormous volumes of security-relevant data. The increasing complexity of these infrastructures, combined with high-speed data transmission and connectivity demands, necessitates advanced monitoring and threat detection. SIEM platforms help consolidate logs, monitor traffic anomalies, and correlate events in real time, enabling IT and telecom companies to maintain network reliability and service continuity.
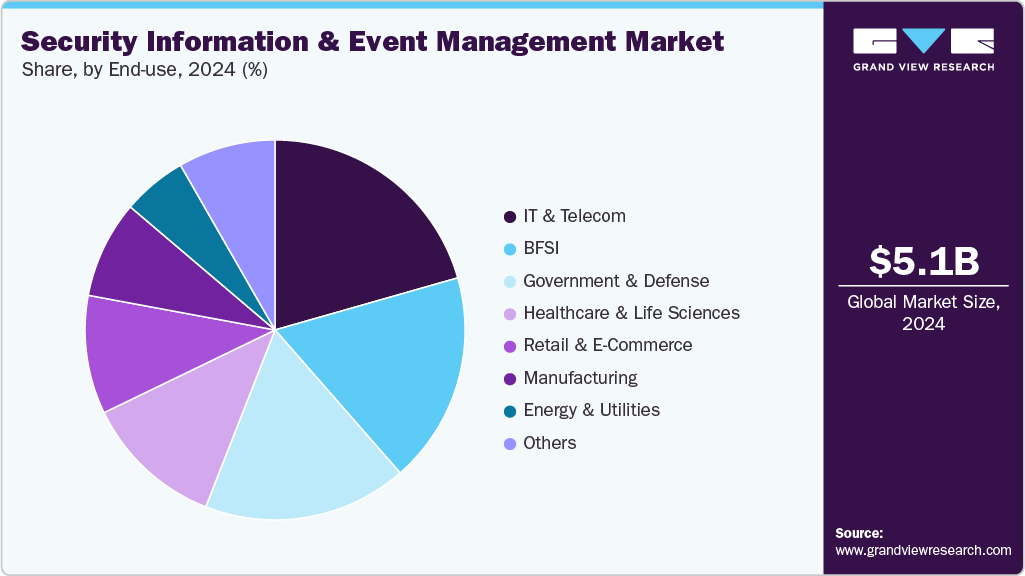
The government & defense segment is expected to grow at a significant CAGR over the forecast period.Cyber threats targeting government and defense sectors are becoming increasingly sophisticated, including Advanced Persistent Threats (APTs), insider attacks, and supply chain compromises. SIEM solutions integrated with AI/ML-based analytics, threat intelligence feeds, and UEBA (User and Entity Behavior Analytics) enable proactive threat detection and faster response, helping organizations mitigate risks before critical damage occurs.
Regional Insights
North America dominated the global market with the largest revenue share of 31.3% in 2024, driven by the high adoption of advanced cybersecurity frameworks by enterprises. Organizations in the region are increasingly deploying AI-enabled and automated threat detection tools within SIEM platforms to protect critical infrastructure, financial systems, and sensitive data from sophisticated cyberattacks, fostering strong market growth.
U.S. Security Information and Event Management Market Trends
The security information and event management (SIEM) market in the U.S. is expected to grow significantly at a CAGR of 10.3% from 2025 to 2033. Stringent regulatory and compliance mandates such as HIPAA, GDPR for US-EU operations, and the CCPA are compelling organizations to adopt SIEM solutions for real-time monitoring, logging, and reporting of security incidents. The need to avoid regulatory penalties and safeguard customer trust fuels adoption among enterprises and SMEs alike.
Europe Security Information And Event Management Market Trends
The security information and event management (SIEM) market in Europe is anticipated to register considerable growth from 2025 to 2033, driven by rising government and enterprise investments in cybersecurity infrastructure. Countries across the EU are increasingly funding initiatives for digital resilience, critical infrastructure protection, and cross-border threat intelligence sharing, encouraging organizations to implement comprehensive SIEM platforms.
The UK security information and event management (SIEM) market is expected to grow rapidly in the coming years, owing to the increasing frequency of ransomware and phishing attacks targeting businesses of all sizes. The need for centralized threat monitoring, rapid incident response, and proactive vulnerability management pushes organizations to adopt SIEM solutions extensively
The Germany security information and event management (SIEM) market held a substantial market share in 2024 due tothe industry 4.0 adoption in manufacturing and critical infrastructure sectors, which requires robust security monitoring of OT (Operational Technology) and IT systems. SIEM solutions help organizations detect anomalies, prevent industrial cyberattacks, and ensure continuity of operations.
Asia Pacific Security Information And Event Management MarketTrends
Asia Pacific security information and event management (SIEM) held a significant share in the global market in 2024, due to rapid digital transformation and cloud adoption among enterprises. Organizations are increasingly moving operations to hybrid IT and cloud platforms, creating a demand for centralized security monitoring, threat detection, and compliance management provided by SIEM solutions.
The Japan security information and event management (SIEM) market is expected to grow rapidly in the coming years. Cybersecurity initiatives by the government and focus on protecting critical industries like automotive, electronics, and finance drive SIEM adoption. The emphasis on real-time threat intelligence and incident response to mitigate sophisticated attacks supports robust market growth.
The China security information and event management (SIEM) market held a substantial market share in 2024, due to the rise of large-scale digital ecosystems and smart city projects, which increase the number of connected devices and the potential attack surface. SIEM platforms are increasingly used to monitor networks, detect threats, and ensure regulatory compliance in this rapidly digitizing environment.
Key Security Information and Event Management Company Insights
Key players operating in the security information and event management (SIEM) industry are Splunk LLC, IBM Corporation, Exabeam, Securonix, and Sumo Logic. The companies are focusing on various strategic initiatives, including new product development, partnerships & collaborations, and agreements to gain a competitive advantage over their rivals. The following are some instances of such initiatives.
-
In August 2025, LevelBlue has finalized its acquisition of U.S.-based cybersecurity managed detection and response (MDR) provider Trustwave. The merger combines LevelBlue’s strengths in network security, strategic risk management, and threat intelligence with Trustwave’s MDR services, Fusion Security Operations Platform, offensive security offerings, and SpiderLabs threat intelligence team. The unified company aims to streamline operations, enhance response capabilities, optimize advanced cyber technologies, and provide integrated protection across cloud, on-premises, and hybrid environments.
-
In July 2025, Rapid7 introduced Incident Command, a next-generation SIEM designed to extend the capabilities of its Command Platform. The new solution integrates attack surface management, threat detection, and response within a unified framework, powered by Agentic AI workflows built on SOC playbooks and continuously refined in real-world use. Using the platform’s data mesh, Incident Command combines Surface Command for attack surface context with Intelligence Hub for curated threat insights, enabling analysts to investigate and respond with greater speed, precision, and efficiency.
-
In May 2025, Exabeam expanded its global partnership with Inspira Enterprise, an India-based cybersecurity, data analytics, and AI services company operating across North America, ASEAN, the Middle East, India, and Africa. Under the renewed collaboration, Inspira will provide the full range of Exabeam solutions both as a managed security services provider (MSSP) and an authorized reseller, strengthening its ability to deliver advanced security offerings to organizations worldwide.
Key Security Information And Event Management Companies:
The following are the leading companies in the security information and event management market. These companies collectively hold the largest market share and dictate industry trends.
- Exabeam
- Fortinet, Inc.
- Fortra, LLC.
- IBM Corporation
- LevelBlue
- Logpoint
- ManageEngine
- Trellix
- NetWitness LLC.
- Open Text Corporation
- Rapid7
- Securonix
- SolarWinds Worldwide, LLC Splunk LLC
- Splunk LLC
- Sumo Logic
Security Information And Event Management Market Report Scope
Report Attribute
Details
Market size in 2025
USD 5.83 billion
Revenue forecast in 2033
USD 18.22 billion
Growth Rate
CAGR of 15.3% from 2025 to 2033
Actual data
2021 - 2024
Forecast period
2025 - 2033
Quantitative units
Revenue in USD billion and CAGR from 2025 to 2033
Report enterprise size
Revenue forecast, company share, competitive landscape, growth factors, and trends
Segments covered
Solution, deployment, enterprise size, end-use, region
Regional scope
North America; Europe; Asia Pacific; Latin America; Middle East & Africa
Country scope
U.S.; Canada; Mexico; UK; Germany; France; China; India; Japan; Australia; South Korea; Brazil; UAE; Kingdom of Saudi Arabia; South Africa
Key companies profiled
Exabeam; Fortinet, Inc.; Fortra, LLC.; IBM Corporation; LevelBlue; Logpoint; ManageEngine; Trellix; NetWitness LLC.; Open Text Corporation; Rapid7; Securonix; SolarWinds Worldwide, LLC; Splunk LLC; Sumo Logic
Customization scope
Free report customization (equivalent to 8 analysts working days) with purchase. Addition or alteration to country, regional & segment scope.
Pricing and purchase options
Avail customized purchase options to meet your exact research needs. Explore purchase options
Global Security Information And Event Management Market Report Segmentation
This report forecasts revenue growth at the global, regional, and country levels and provides an analysis of the latest industry trends in each of the sub-segments from 2021 to 2033. For this study, Grand View Research has segmented the global security information and event management market report based on solution, deployment, enterprise size, end-use, and region:
-
Solution Outlook (Revenue, USD Billion, 2021 - 2033)
-
Software
-
Services
-
-
Deployment Outlook (Revenue, USD Billion, 2021 - 2033)
-
Cloud
-
On-premise
-
-
Enterprise Size Outlook (Revenue, USD Billion, 2021 - 2033)
-
Small and Medium-Sized Enterprises (SMEs)
-
Large enterprises
-
-
End-use Outlook (Revenue, USD Billion, 2021 - 2033)
-
BFSI
-
IT and Telecom
-
Retail & E-commerce
-
Healthcare and Life Sciences
-
Manufacturing
-
Government & Defense
-
Energy & Utilities
-
Others
-
-
Regional Outlook (Revenue, USD Billion, 2021 - 2033)
-
North America
-
U.S.
-
Canada
-
Mexico
-
-
Europe
-
UK
-
Germany
-
France
-
-
Asia Pacific
-
China
-
India
-
Japan
-
South Korea
-
Australia
-
-
Latin America
-
Brazil
-
-
Middle East & Africa
-
UAE
-
Saudi Arabia
-
South Africa
-
-
Frequently Asked Questions About This Report
b. The software segment led the market with a 64.5% revenue share in 2024, driven by growing demand for SIEM solutions integrated with SOAR to address the cybersecurity skills gap.
b. Some key players operating in the security information and event management (SIEM) market include Exabeam, Fortinet, Inc., Fortra, LLC., IBM Corporation, LevelBlue, Logpoint, ManageEngine, Trellix, NetWitness LLC., Open Text Corporation, Rapid7, Securonix, SolarWinds Worldwide, LLC, Splunk LLC, Sumo Logic
b. Key factors driving the security information and event management market growth include the increasing sophistication and frequency of cyberattacks across industries. As organizations face advanced threats such as ransomware, phishing, and insider attacks, the need for real-time monitoring, threat detection, and rapid incident response becomes critical.
b. The global SIEM market is expected to grow at a compound annual growth rate of 15.3% from 2025 to 2033 to reach USD 18.22 billion by 2033.
b. The global security information and event management market size was estimated at USD 5.12 billion in 2024 and is expected to reach USD 5.83 billion in 2025.
Share this report with your colleague or friend.
Need a Tailored Report?
Customize this report to your needs — add regions, segments, or data points, with 20% free customization.

ISO 9001:2015 & 27001:2022 Certified
We are GDPR and CCPA compliant! Your transaction & personal information is safe and secure. For more details, please read our privacy policy.
Trusted market insights - try a free sample
See how our reports are structured and why industry leaders rely on Grand View Research. Get a free sample or ask us to tailor this report to your needs.