- Home
- »
- Next Generation Technologies
- »
-
Zero Trust Security Market Size, Industry Report, 2030GVR Report cover
![Zero Trust Security Market Size, Share & Trends Report]()
Zero Trust Security Market (2025 - 2030) Size, Share & Trends Analysis Report By Authentication (Single-factor, Multi-factor), By Type, By Deployment (Cloud, On-premises), By Enterprise Size, By End Use, By Region, And Segment Forecasts
- Report ID: GVR-4-68038-292-1
- Number of Report Pages: 100
- Format: PDF
- Historical Range: 2017 - 2024
- Forecast Period: 2025 - 2030
- Industry: Technology
- Report Summary
- Table of Contents
- Interactive Charts
- Methodology
- Download FREE Sample
-
Download Sample Report
Zero Trust Security Market Summary
The global zero trust security market size was estimated at USD 36.96 billion in 2024 and is anticipated to reach USD 92.42 billion by 2030, growing at a CAGR of 16.6% from 2025 to 2030. The increasing adoption of cloud computing, remote work trends, and the surge in ransomware and insider threats drives the market growth.
Key Market Trends & Insights
- North America zero trust security market dominated with a revenue share of over 37% in 2024.
- The U.S. zero trust security market is expected to grow at a significant CAGR from 2025 to 2030.
- By authentication, the single-factor segment led the market in 2024, accounting for a revenue share of over 53% in 2024.
- By type, the endpoint security segment accounted for the largest market revenue share in 2024.
- By deployment type, the cloud segment accounted for the largest market revenue share in 2024.
Market Size & Forecast
- 2024 Market Size: USD 36.96 Billion
- 2030 Projected Market Size: USD 92.42 Billion
- CAGR (2025-2030): 16.6%
- North America: Largest market in 2024
- Asia Pacific: Fastest growing market
Enterprises and government agencies are investing heavily in Zero Trust solutions, including multi-factor authentication (MFA), micro-segmentation, identity and access management (IAM), and endpoint security. Small and medium enterprises (SMEs) are also recognizing the benefits of Zero Trust architectures, driving demand for cost-effective and scalable solutions. As businesses continue to shift toward digital transformation, the zero trust security market is poised for exponential growth.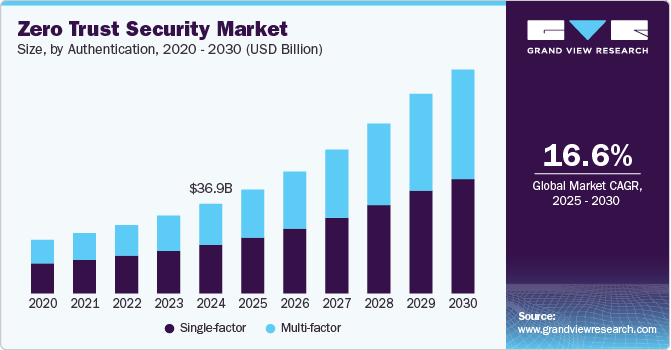
The risk of cyberthreat is increasing considerably as cyber threat actors continue to explore vulnerabilities within an organization's IT infrastructure. Cyber threat actors gain access to critical information through vulnerabilities while maintaining anonymity. Cyber threat actors launch attacks such as persistent campaigns, advanced malware, spear-phishing, and watering holes to exploit organizational growth. For instance, according to research by Check Point Software Technologies Ltd., global cyberattacks increased by 28% in the third quarter of 2022 compared to 2021. Globally, the average number of weekly attacks per organization exceeded 1,100.
Over the years, targeted attacks on organizations across the globe have increased significantly. Attackers infiltrate a target organization's network infrastructure through endpoints, cloud-based applications, and other vulnerable networks. Such targeted attacks negatively impact a business's critical operations, leading to financial losses, loss of sensitive customer information, and loss of intellectual property. According to a sponsored study conducted by Trend Micro Incorporated with Quocirca, the most common objective of a targeted cyberattack is to impact organizational financial gains. Thus, a proactive detection layer is paramount to prevent the risk of losing regulated personal data, intellectual property, and economic loss. Through zero security principles, proactive detection and mitigation of cyber threats can be achieved by identifying the behavior of users infiltrating any network.
Authentication Insights
The single-factor segment led the market in 2024, accounting for a revenue share of over 53% in 2024. This growth is driven by the rising adoption of passwordless authentication, biometric-based access controls, and the increasing demand for cost-effective security solutions among SMEs. Organizations are prioritizing user-friendly authentication methods to enhance security while reducing friction in user experience. Additionally, regulatory compliance requirements and the integration of AI-driven authentication technologies are fueling market expansion. As businesses shift towards cloud-based and remote work environments, the need for seamless yet secure authentication solutions will further propel the demand for advanced SFA solutions in the coming years.
The multi-factor segment is predicted to grow significantly in the forecast years. This growth is fueled by the rising frequency of cyberattacks, phishing attempts, and credential-based breaches, which push organizations to adopt stronger authentication measures. The increasing adoption of cloud computing, remote work, and BYOD (Bring Your Own Device) policies has further accelerated the demand for MFA solutions, ensuring enhanced security beyond traditional passwords. Regulatory mandates like GDPR, CCPA, and the U.S. Executive Order on Cybersecurity are driving enterprises to implement MFA for compliance.
Type Insights
The endpoint security segment accounted for the largest market revenue share in 2024. The growth of the endpoint segment can be attributed to its benefits which include improved patch management, preventing insider threats, filtering content web, reducing AI threats, and streamlining cybersecurity, among others. Moreover, the companies in the market have been developing an enhanced solution to get better traction. Companies are involved in various strategic initiatives, including partnerships, acquisitions, and mergers. For instance, in January 2023, Xcitium cybersecurity provider announced a partnership with Carrier SI, a communication solution provider. The partnership is aimed at offering enhanced and affordable endpoint security. Moreover, Carrier SI customers will now have access to the endpoint cybersecurity technology capable of containing known and unknown cyberattacks.
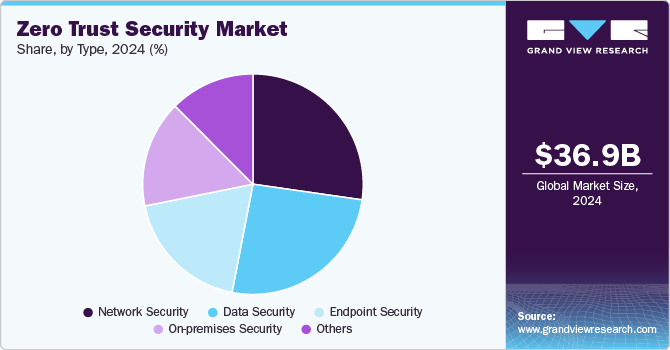
The on-premises security segment is predicted to foresee significant growth in the coming years. This growth is driven by the increasing need for data sovereignty, regulatory compliance, and enhanced control over security infrastructure, especially among large enterprises and government organizations. Industries handling sensitive data, such as finance, healthcare, and defense, prefer on-premises solutions to mitigate risks associated with cloud vulnerabilities. Additionally, the rising threat of cyberattacks, insider threats, and ransomware has fueled demand for dedicated, in-house security architectures.
Deployment Insights
The cloud segment accounted for the largest market revenue share in 2024. The growth of the cloud-based segment can be attributed to the comfort and convenience the cloud-based deployment offers, which includes the lesser need for in-house resources, less need for upfront costs, continuous monitoring, flexible options, automatic backups, and effective patch management, among others. The flexibility and scalability of cloud-based deployment have been among the major factors that contributed to the growth of the cloud-based deployment of the market over 2025-2030.
The on-premises segment is expected to witness significant growth in the coming yearsdue to a high preference for this type of deployment. Organizations prefer to keep confidential data in-house rather than turning it over to a cloud provider. Moreover, on-premises solutions allow hands-on ownership and control of security monitoring, which offers a flexible and adaptive security program. This is expected to increase the demand for on-premises deployment over the forecast period. However, enterprises are migrating from on-premises to cloud-based solutions due to cost-effectiveness benefits.
Enterprise Size Insights
The large enterprises segment accounted for the largest market revenue share in 2024owing to complex networking, programs, and endpoints of large-scale companies that need robust solutions to safeguard data by continuously validating and recording authentication in real-time. Companies rely on only adhering to compliance and entrusting authorized users with a higher risk of an internal breach. The compliant network does not guarantee a secure environment, as the threat to breach is not merely external but also could be by internal trusted sources. The zero-trust security model regards enterprise-authorized users with zero trust and provides the least privileged access to the users.
The SMEs segment is anticipated to exhibit the fastest CAGR over the forecast period. The COVID-19 pandemic affected both large- and small-scale vendors as cases of data breaches increased while employees resorted to the remote working environment. Small- and medium-sized banking, financial institutions, IT, manufacturing, telecom, and retail companies are targeted as they need robust security solutions. Zero trust security ensures that the user with correct credentials is an internal and trusted user, not hackers relying on phishing and other methods to gain illegitimate access to login credentials. Thereby, the adoption of a zero-trust security model is increasing among SMEs for implementing multi-level authorization verification.
End Use Insights
The IT & telecom segment accounted for the largest market revenue share in 2024due to the sector's intricate IT infrastructure demands. Increased preference for cloud-based infrastructure and digital applications to procure information and facilitate business drives the need for unified, secure access and network solutions. In addition, the telecom industry incumbents primarily provide data transfer services and spend on several security-related technologies. With the increasing awareness about the benefits and applications of zero-trust security, the adoption of this model is expected to grow significantly.
The healthcare segment is anticipated to exhibit the fastest CAGR over the forecast period. Continued innovation and implementation of technologies, such as telehealth services and analytics, to facilitate effective communication between end-users and entities are driving the need for secure network infrastructure services. Moreover, the increasing instances of cyber-attacks across healthcare IT infrastructures created the need for an advanced security framework for protecting critical information. These factors are expected to accelerate the demand for zero-trust security in the healthcare sector.
Regional Insights
North America zero trust security market dominated with a revenue share of over 37% in 2024. The rising demand for solutions pertaining to the zero-trust security model due to the increasing security spending by the government and public authorities is expected to drive the regional market. Furthermore, the increased adoption of the Internet of Things (IoT), AI, and digital technology by SMEs and large enterprises and the increasing stringency in standards and policies for maintaining data privacy and security are contributing to regional market growth.
U.S. Zero Trust Security Market Trends
The U.S. zero trust security market is expected to grow at a significant CAGR from 2025 to 2030, driven by increasing cyber threats, stringent regulatory requirements, and rapid digital transformation across industries. The surge in ransomware attacks, data breaches, and insider threats has compelled enterprises and government agencies to adopt zero-trust architectures for enhanced security. Additionally, the rise of cloud computing, remote work, and IoT has increased the demand for identity-centric security solutions, multi-factor authentication (MFA), and micro-segmentation.
Europe Zero Trust Security Market Trends
The zero trust security market in the Europe is expected to witness significant growth over the forecast period, driven by rising cyber threats, strict regulatory frameworks, and increased cloud adoption. The enforcement of GDPR, NIS2 Directive, and other data protection laws is pushing enterprises to implement zero-trust architectures to ensure compliance and mitigate security risks. Additionally, the rise in state-sponsored cyberattacks and ransomware incidents has led businesses and government agencies to prioritize Zero Trust frameworks.
Asia Pacific Zero Trust Security Market Trends
The zero trust security market in the Asia Pacific region is anticipated to register the fastest CAGR over the forecast period, driven by increasing cyber threats, rapid digital transformation, and stringent regulatory policies across major economies like China, India, Japan, and Australia. Governments are strengthening cybersecurity frameworks, with initiatives like India’s Personal Data Protection Act (PDPA) and China’s Cybersecurity Law, compelling organizations to adopt zero-trust architectures.
Key Zero Trust Security Company Insights
Some key players in the zero trust security market include Broadcom, Inc., Fortinet, Inc., Palo Alto Networks, Inc., IBM Corporation, and Microsoft.
-
Broadcom Inc. is a key player in the zero trust security market, leveraging its expertise in enterprise security, network protection, and identity management. Through its Symantec division, Broadcom offers advanced zero trust solutions that include multi-factor authentication (MFA), endpoint security, network micro-segmentation, and threat intelligence. The company’s AI-driven security analytics help organizations detect and prevent sophisticated cyber threats in real-time. With increasing demand for cloud-based zero trust architectures, Broadcom has expanded its portfolio to support secure access service edge (SASE) frameworks and zero trust network access (ZTNA) solutions.
-
Fortinet, Inc. is a foremost player in the zero trust security market, offering a comprehensive portfolio of Zero Trust Network Access (ZTNA), endpoint security, and identity-based access solutions. Its FortiNAC and FortiAuthenticator solutions enable enterprises to implement network segmentation, multi-factor authentication (MFA), and continuous verification to reduce attack surfaces. Fortinet’s AI-driven threat intelligence and Secure Access Service Edge (SASE) solutions further enhance Zero Trust capabilities, ensuring secure access to applications and data across hybrid environments.
Key Zero Trust Security Companies:
The following are the leading companies in the zero trust security market. These companies collectively hold the largest market share and dictate industry trends.
- Broadcom, Inc.
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- IBM Corporation
- Microsoft
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Check Point Software Technology Ltd.
- CrowdStrike, Inc.
- Forcepoint
Recent Developments
-
In December 2024, Cognizant and Zscaler announced an expanded partnership aimed at helping enterprises across industries streamline and enhance their security posture with an AI-powered Zero Trust cloud security platform. This collaboration addresses evolving cyber threats by delivering coordinated services and solutions that reduce security complexity, strengthen defenses, and provide cost-effective, scalable protection. By combining their expertise, Zscaler and Cognizant enable organizations to modernize cybersecurity strategies while ensuring rapid and comprehensive security transformation.
-
In October 2024, Alkira Inc., a prominent player in Network Infrastructure as a Service, unveiled Alkira Zero Trust Network Access (ZTNA), a cutting-edge cloud-based solution designed to revolutionize secure enterprise access from anywhere. Scheduled for general availability in Q4 2024, Alkira ZTNA integrates zero trust principles with Alkira’s expertise in network infrastructure, providing a seamless, end-to-end security platform. This innovative service ensures robust protection and streamlined connectivity without compromising network performance and efficiency, making it a game-changer for modern enterprises.
-
In January 2024, Zscaler, Inc., a leader in cloud security, introduced Zscaler Zero Trust SASE, the industry’s first single-vendor SASE solution powered by Zscaler Zero Trust AI. Designed to simplify Zero Trust implementation across users, devices, and workloads, this solution helps organizations reduce costs and complexity. Additionally, Zscaler announced the general availability of its Zero Trust SD-WAN solution and a portfolio of plug-and-play appliances, enabling businesses to modernize secure connectivity for branch offices, factories, and data centers. By eliminating the need for VPNs and traditional firewalls, Zscaler’s solutions provide a more efficient, scalable, and secure approach to enterprise networking.
Zero Trust Security Market Report Scope
Report Attribute
Details
Market size value in 2025
USD 42.91 billion
Revenue forecast in 2030
USD 92.42 billion
Growth rate
CAGR of 16.6% from 2025 to 2030
Historical data
2017 - 2024
Forecast period
2025 - 2030
Quantitative units
Revenue in USD million and CAGR from 2025 to 2030
Report coverage
Revenue forecast, company ranking, competitive landscape, growth factors, and trends
Segments covered
Authentication, type, deployment, enterprise size, end use, region
Regional scope
North America; Europe; Asia Pacific; Latin America; MEA
Country scope
U.S.; Canada; Mexico; Germany; U.K.; France; China; India; Japan; Australia; South Korea; Brazil; UAE; South Africa; KSA
Key companies profiled
Broadcom; Inc.; Fortinet, Inc.; Palo Alto Networks, Inc.; IBM Corporation; Microsoft; Cisco Systems Inc.; Cloudflare, Inc.; Check Point Software Technology Ltd.; CrowdStrike Inc.; Forcepoint
Customization scope
Free report customization (equivalent up to 8 analysts working days) with purchase. Addition or alteration to country, regional & segment scope.
Pricing and purchase options
Avail customized purchase options to meet your exact research needs. Explore purchase options
Global Zero Trust Security Market Report Segmentation
This report forecasts revenue growth at global, regional, and country levels and provides an analysis of the latest industry trends in each of the sub-segments from 2017 to 2030. For this study, Grand View Research has segmented the global zero trust security market report based on authentication, type, deployment, enterprise size, end use, and region.
-
Authentication Outlook (Revenue, USD Million, 2017 - 2030)
-
Single-factor
-
Multi-factor
-
-
Type Outlook (Revenue, USD Million, 2017 - 2030)
-
Network Security
-
Data Security
-
Endpoint Security
-
On-premises Security
-
Others
-
-
Deployment Outlook (Revenue, USD Million, 2017 - 2030)
-
Cloud
-
On-Premises
-
-
Enterprise Size Outlook (Revenue, USD Million, 2017 - 2030)
-
SMEs
-
Large Enterprises
-
-
End Use Outlook (Revenue, USD Million, 2017 - 2030)
-
BFSI
-
Healthcare
-
Retail
-
IT & Telecom
-
Others
-
-
Regional Outlook (Revenue, USD Million, 2017 - 2030)
-
North America
-
U.S.
-
Canada
-
Mexico
-
-
Europe
-
U.K.
-
Germany
-
France
-
-
Asia Pacific
-
China
-
India
-
Japan
-
Australia
-
South Korea
-
-
Latin America
-
Brazil
-
-
MEA
-
UAE
-
South Africa
-
KSA
-
-
Frequently Asked Questions About This Report
b. The global zero-trust security market size was estimated at USD 36.96 billion in 2024 and is expected to reach USD 42.91 billion in 2025.
b. The global zero-trust security market is expected to grow at a compound annual growth rate of 16.6% from 2025 to 2030 to reach USD 92.42 billion by 2030.
b. North America emerged as a dominant regional zero-trust security market capturing 38.5% of the overall zero-trust security revenue share in 2024.
b. Some key players operating in the zero-trust security market include Broadcom, Inc., Fortinet, Inc., Palo Alto Networks, Inc., IBM Corporation, Microsoft, Cisco Systems, Inc., Cloudflare, Inc., Check Point Software Technology Ltd., CrowdStrike, Inc., Forcepoint
b. Key factors that are driving the zero-trust security market growth include the increasing adoption of cloud computing, remote work trends, and the surge in ransomware and insider threats. Enterprises and government agencies are investing heavily in Zero Trust solutions, including multi-factor authentication (MFA), micro-segmentation, identity and access management (IAM), and endpoint security.
Share this report with your colleague or friend.
Need a Tailored Report?
Customize this report to your needs — add regions, segments, or data points, with 20% free customization.

ISO 9001:2015 & 27001:2022 Certified
We are GDPR and CCPA compliant! Your transaction & personal information is safe and secure. For more details, please read our privacy policy.
Trusted market insights - try a free sample
See how our reports are structured and why industry leaders rely on Grand View Research. Get a free sample or ask us to tailor this report to your needs.